
Mobile Security
Mobile Threat Prevention
Prevent, protect, detect, and respond to cybersecurity threats including zero-day, phishing, and network attacks targeting mobile devices, applications, and operating systems to minimize risk and prevent data loss across customer data, intellectual property, and core systems.
Achieve Compliance
Balances data privacy with security to reduce the risk of data theft, credential loss and achieve regulatory compliance with GDRP, PCI, HIPAA, etc.
Safeguard Corporate Data & BYOD Devices
Protects both corporate-owned and bring-your-own devices (BYOD) from advanced persistent threats, including device, network, phishing, and app attacks, to ensure secure data access and protection.
Gain Visibility into Your Mobile Footprint with Mobile Threat Detection (MTD)

Mobile Application Vetting
Detect non-compliant applications with application vetting that assesses applications’ security and privacy postures. As an organization, you can design your own “application compliance” policy, build a catalogue of accepted apps and versions and monitor endpoints through it. In addition, you can trigger actions (locally on MTD or via MDM) on out of compliance application detections.

App-Web-Network-Device Protection
Mobile Security utilizes on-device machine learning technologies to detect both known and unknown threats by monitoring mobile device behavior, accurately identifying malware-like apps, anomalous network traffic, and phishing attacks, and provides secure connectivity and protection even when the endpoint is offline.

Anti-Phishing Protection
Mobile Security offers on-device anti-phishing protection on all supported platforms (iOS, Android) and on-device, local VPN for real-time processing of traffic without relying on an external service, thereby effectively preventing email phishing attacks.

Device Assessment & Visibility
On top of monitoring vulnerabilities on your device and providing MITRE mapping, Mobile Security monitors for vulnerabilities and gives visibility into missing encryption, jailbreaking, root access, and outdated devices that are no longer receiving the latest security updates. Deep cloud-based analysis enables organizations to gain insight into the compliance and privacy-related practices of any application running within their operations.

Web Content Filtering
Web content filtering warns and prevents users from accessing potentially harmful websites and links, such as malware, phishing, botnets, and suspicious domains, or websites that violate your organization’s standards.

Integration with Mobile Device Management (MDM) Solutions
MDM integration enhances mobile security features and enables mobile device security policies to be enforced automatically.
Why choose Mobile Security?
Mobile Security ensures safe and secure access to corporate data, safeguarding both corporate-owned data and BYOD devices from modern attack vectors, including zero-day, phishing, and network attacks, by detecting both known and unknown threats.
The solution seamlessly integrates with mobile device management (MDM) solutions enabling IT teams to automatically enforce mobile device security policies.
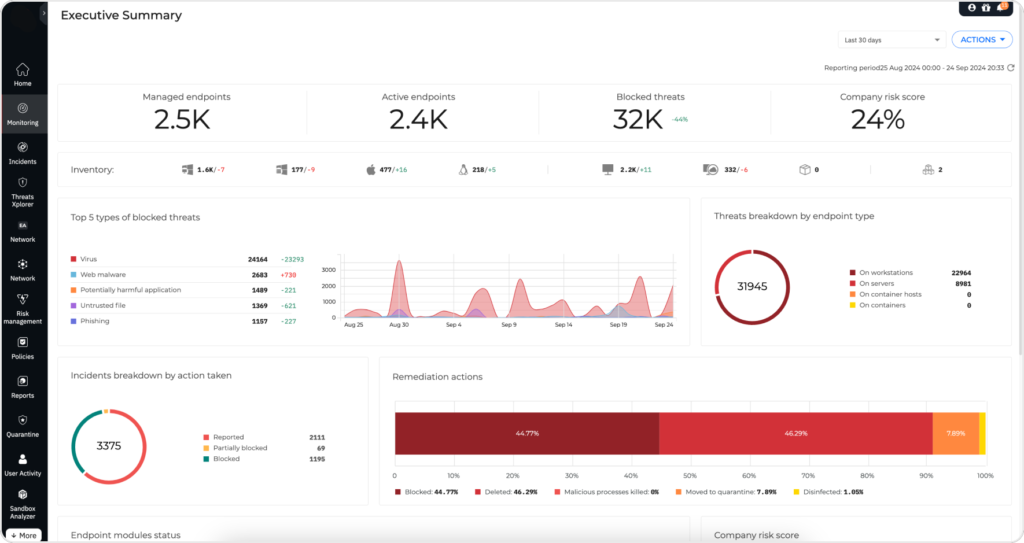

Unified Security, Seamless Integration
Mobile Security integrates with the unified console, enabling enterprise businesses and their customers to extend security beyond traditional endpoints. In addition, seamless integration with existing mobile device management (MDM) solutions enables security teams to efficiently manage and streamline security operations from a single platform.

Leverage industry-Leading Antimalware
We consistently receive top rankings by independent evaluations from organizations such as MITRE, AV-Comparatives, or AV-TEST. The company achieved the most #1 placements in AV-Comparatives Enterprise tests and maintained hundred percent detection and highest level of description 3 years in a row in the MITRE Enginuity ATT&CK Evaluations.

End-to-End Visibility
With Mobile Security your IT teams have end-to-end insight and visibility across all platforms and applications.
Frequently Asked Questions
Mobile Security is a mobile threat defense (MTD) solution, not a mobile device management (MDM) solution.
Mobile Security detects known and unknown threats by analyzing the behavior of a mobile device and then accurately identifies mobile system deviations, applications that behave as malware, anomalous network traffic, and advanced phishing attacks. Furthermore, machine learning is delivered on-device, securing it even if the endpoint is not connected to the network.
Mobile device management (MDM) solutions provide device management capabilities to remotely control, track and encrypt devices and enforce policies (e.g., wipe or lock the device if stolen). It is important to note that Mobile Security seamlessly integrates with MDM solutions. Empowering IT teams with the ability to automatically enforce mobile device policies.
Mobile Security takes a privacy-centered approach, ensuring users have a clear understanding of the data collected and utilized for threat intelligence through customizable user settings and transparent visibility.
By conducting detection directly on the device, Mobile Security eliminates the need to send private information to the cloud, ensuring user privacy is maintained.
Mobile Security is an optional cloud add-on available to any of our endpoint security solutions.
Yes, Mobile Security can integrate with MDMs for better protection and easier deployment.
Specifications
The minimum operating system version is iOS 11 or Android 5.1.
The minimum operating system version is iOS 11 or Android 5.1.
The local Virtual Private Network (VPN) functionality requires iOS 11 and higher or Android 6 and higher.
A 64-bit version of the device is required for iOS devices.
For full Knox device action support, Android version 7 and Knox version 2.7 or later are required.
Internet connection required for threat reporting, configuration updates, version updates and deep threat analysis on cloud.
Android support for Chromebook requires the Chromebook to support Android apps and the Google Play Store.
Supported Browsers (Requires HTML 5) :
· Chrome – Recommended Current Version
· Safari Current Version (not tested)
· Firefox Current Version (not tested)
MDM Systems
· VMWare Workspace ONE UEM MDM 8.3
· BlackBerry Dynamics : BlackBerry Dynamics 1.0
· BlackBerry’s UEM MDM (BES) 12.7 UEM
· Business Concierge MDM 12.3
· Citrix MDM 10.4
· IBM MaaS360 10.65
· MobileIron MDM Core 8 Cloud (Current Version)
· SOTI MobiControl 14.1
· MDM System Passwords: Do not use a colon (:) in the MDM password field, or use `password` as a password value.
· SIEM : Any SIEM that has a JSON Syslog input capability