
INTEGRITY MONITORING
Monitor Data Fidelity, Meet Regulations
Monitor confidential and regulated data and configurations across files, directories, and applications to ensure their fidelity and meet compliance standards with frameworks such as PCI DSS, ISO 27001, HIPAA, GDPR and more.
Maximum Operational Efficiency
Respond to security events quickly and efficiently with actionable recommendations, reducing time and effort needed to identify anomalies and eliminating alert fatigue. Minimize performance impact while supporting change and risk management efforts.
Prevent Security Events
Identify meaningful configuration changes in real time which might indicate an integrity incident or security event, empowering security teams to act against malicious activity and prevent damage.
Gain Visibility into Unauthorized Configuration Changes
Real-Time Scanning
Real-time scanning provides security teams visibility into all the entities in an environment with insights visible on the Integrity Monitoring Events page.

Corrective, Flexible Actions
Gain flexibility to responses by controlling actions to be automated or manual based on defined rules and recommendations, thereby also reducing alert fatigue.

Monitoring Rulesets
Apply certain rules and rulesets to your endpoints and define the areas and specific parameters/entities your security team wants monitored. Create rulesets based on any rules to work together as a single rule.

Performance Optimization
An intuitive interface and turnkey confirmations reduce time and effort spent on configuration.
Why choose Integrity Monitoring?
Integrity Monitoring is an out-of-the-box corrective solution offering more than file monitoring by assessing entities (File, Directories, Registry, Installed Apps, etc.) across protected assets throughout the entire organization. The solution provides security teams with actionable recommendations to act on security events quickly and effectively.
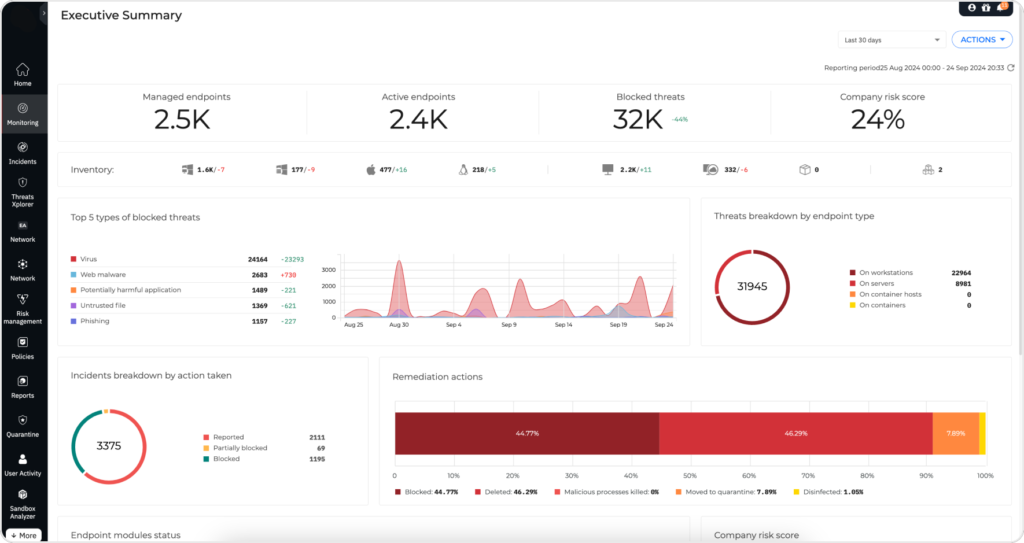

Comprehensive
With Integrity Monitoring your security teams benefit from easy deployment and rapid configuration to quickly start identifying anomalies. Capabilities like automated and guided responses to changes, event categorization to quickly identify the most critical events, and performance optimizations to reduce alert fatigue, realizing rapid returns is made simple by the Business Security approach to comprehensive Integrity Monitoring.

Contextually Aware
Security teams do not have to sort through approved changes to find the most critical event. Integrity Monitoring automatically provides actionable recommendations within context, so security teams have the information they need to act on an event quickly and prevent security incidents.

Unified Security
Unify and streamline security solutions under one platform including Integrity Monitoring, server workload security, container security, endpoint protection, response, and extended detection and response (XDR) to bring together device intelligence across your network.
Frequently Asked Questions
There are many industries that have regulatory frameworks and compliance mandates.
A File Integrity Monitoring solution is a key component of various security frameworks including the Payment Card Industry – Data Security Standard (PCI-DSS), General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and National Institute of Standards and Technology (NIST).
Integrity Monitoring helps ensures that your organization meets compliance and regulatory standards
A File Integrity Monitoring (FIM) solution is a foundational element in Gartner’s Cloud Workload Protection Platform (CWPP) Controls Hierarchy for system integrity assurance.
An FIM solution is an essential element to cloud workload security and the posture of a security stack.
Yes, Integrity Monitoring comes with a default 7-day Data Retention setting. Regulatory frameworks often require longer data retention times; MyCyberIQ offers a Data Retention add-on option to store your events in for:
- 90 days
- 180 days
- 1 year
Specifications / System Requirements
Modules and features are available on all versions of supported operating systems, according to each type of endpoint (Windows, Linux, or macOS).
Minimum: 2.4 GHz single-core CPU Recommended: 1.86 GHz or faster Intel Xeon multi-core CPU
Memory: Minimum free RAM: 512 MB Recommended free RAM: 1 GB HDD space: 1.5 GB of free hard-disk space
Control Center is delivered as a virtual appliance and is available in the following formats:
OVA (compatible with VMware vSphere, View)
XVA (compatible with Citrix XenServer, XenDesktop, VDI-in-a-Box)
VHD (compatible with Microsoft Hyper-V)
Support for other formats and virtualization platforms may be provided on request.